Technology Abuse
Technology Abuse is the new weapon of choice- a form of controlling behaviour that involves the use of technology as a means to harass, coerce or stalk another person. Technology Abuse is also commonly referred to as:
– Technology-facilitated Abuse
– Tech Abuse
– TFA
The act of monitoring, tracking and harassment through technology devices can magnify a victim’s sense of imprisonment and isolation within a relationship, previous relationship or everyday life. Tech abuse makes victims feel as though their perpetrators are omnipresent in their lives and that there’s no escape – even after a relationship has ended.
Due to the borderless and indiscriminate nature of the Internet, anyone can say anything online.
Threats can be upsetting and traumatic to receive, even when made by anonymous people we’ve never met. However, tech abuse can have real-life implications when perpetrated by a spouse or ex-partner. Thanks to the Internet and our increasingly “smart” devices, there are now a frightening number of ways for abusers to control, humiliate and isolate their victims.
Examples of Technology abuse are:
-Abusive messages including e-mails and social media
-Abusive calls such as threats or controlling.
-Sharing intimate photos of someone without their consent (sometimes called revenge porn)
-Making someone prove where they are by sending photos of their location.
-Image-based abuse, when someone shares or threatens to share an intimate image of you without your consent
-Checking someone’s text messages, social media activity or internet activity
-Account takeovers, where someone accesses your online accounts and locks you out of them
-Fake social media accounts, when fake accounts are being used to harass you or post negative comments about you online
-Forbidding someone from having a phone or limiting who they can contact via phone or internet
-Spying on, monitoring, stalking or tracking someone through any type of surveillance device (such as a tracking system or spyware)
-Radio-controlled devices such as drone.
Where Tech Abuse happens.
Technology Abuse as the name suggests is- abuse.
Technology facilitated abuse generally happens when there is a breakdown of a personal relationship or when a restraining order is imposed and is prevalent in Domestic Abuse and Family Violence. Technology Abuse often happens in Coercively controlling relationships.
Technology facilitated abuse is often used in the following situations:
-Workplace related when an employee is asked to leave a job or made redundant
-In a relationship be it domestic partner, marriage, or even friendship
-Relationship separation
-Teenage dating
-A vehicle to promote Racism and far-right views
-Business breakdown
-Financial Hardship
-To discredit a business or an individual
The most recent survey of domestic violence support services in Australia, found that 98% of respondents had clients who had experienced technology-facilitated stalking and abuse including Aboriginal and Torres Strait islanders.
The survey found that technology-facilitated abuse happens across a wide range of platforms, including:
-Text message (80%)
-Facebook (82%)
-Mobile phones (82%)
-Email (52%)
-GPS tracking (29%)
Where we have seen Technology Abuse at Protective Group.
At Protective Group we find the use of Technology Abuse is prevalent in nine out of ten Domestic and Family Violence cases that are referred to us. Technology Abuse isn’t only prevalent when there is a breakdown in a personal relationship but can occur as normal abuse would, just not physical.
In our experience we see Technology abuse happening:
-Spyware being used when martial relationships end. Perpetrators often use children’s personal devices to load spyware software to track their ex-partners – often blaming mental health
-Ex-partners tracking there previous parent through GPS tracking devices on the vehicles and surveillance stalking.
-Secondary school students through “revenge porn”
-Online. Through email, messaging, social media, dating sites, and other platforms. Abusers who commit online harassment often do it to make you feel unsafe, humiliated, scared, or emotionally distressed.
-Cloud based programs where a Perpetrator can monitor their victim via cloud based programs such as icloud.
-Home based networks via WIFI/. For example, an abuser could remotely control the smart locks on your home, limiting your ability to leave the house or to return to it. A video doorbell could be used not only to monitor who comes to the door, but to harass them remotely or, in combination with a smart lock, prevent them from entering the house.
-Spoofing. Spoofing is a term that means masking or hiding one’s actual phone number so that another phone number (chosen by the user) shows up on the recipient’s caller ID.
The majority of Technology Abuse we see on a daily basis is from Domestic and Family violence matters. Far to often we see the perpetrator using easy to access over the country, or bought Online Spyware and GPS tracking devices, often we see the Children the target of where the use of these methods are used:
-GPS trackers inside Children’s toys
-Spyware downloaded on young children’s tablet computers
-racking devices disguised as gifts such as smart watches which have locations apps pre-programmed.
We see each day the perpetrator controls their victim and the physiological and emotional effect it has on the victim, the victim questions themselves every minute of the day “ am I being watched, are they looking at me”.
Even the most inconspicuous devices are often used: baby monitors being pre-programmed to listen to their victim, controlling home WIFI networks to turn on music at 3am in the morning or turning the heating on at the highest temperature.
This Silent Menace is the new frontier being used by the aggressor and they are becoming more cunning and confident each time our assessment team is faced with the silent predator.
Technology Abuse – From the field
“With the onset of COVID-19, we have seen a triple-digit increase in our Technology Abuse services. The ease of purchasing trackers and spyware software from retailers and Online is driving an increase in the use of smart technology. We are increasingly seeing perpetrators being creative in how they track and control their victims.”
“The ease of purchasing trackers and spyware software from retailers and Online is driving an increase in the use of smart technology.”
“We need to adapt to the ever-changing landscape, our field assessment team are meeting daily to share their experiences to ensure we are not only disrupting Technology Abuse but eliminating it.”
Stephen Wilson
CEO at Protective Group
Identifying technology abuse
Often a victim may question themselves if Technology Abuse is happening to them; “Could it just be a coincidence they always know where I am and what I’m doing”.
The following is a guide to some of the key behaviours that could indicate you are a victim of technology abuse.
Bullying and harassment: Sending insulting or threatening texts or social media messages; putting you down in social media posts; tagging you in hurtful posts or photos; posting embarrassing photos of you.
Monitoring and stalking: Stealing or demanding to know your passwords; looking through your phone or computer without permission; using location tagging or spyware to monitor and track you; posing as you online; remotely controlling your smart home devices to intimidate you
Sexual coercion: Demanding you take or send explicit photos or videos you aren’t comfortable with; sending you explicit photos or videos without your consent; sharing your photos or videos with others; taking photos or videos of you without your knowledge
Possessiveness and control: Deciding who you can follow or be friends with online; controlling who you can text or message; demanding your constant attention through technology; making you feel unsafe for not responding to messages immediately
If you are facing Technology Abuse, know that it is not your fault, it is not physical but just as damaging.
You have the right to privacy online and offline. You also have the right to decide for yourself how you use photos, social media, and smart home devices and other technology, as well as who you communicate with and how often. Above all, you have the right to feel safe and respected.
We also thank 2020 Stella prize winner Jess Hill for allowing Protective Group to share our story on technology-facilitated abuse in the 3-part documentary series See What You Made Me Do. The Silver Logie nominee series explores one of the most complex and urgent issues of our time – domestic abuse. Presented by investigative journalist Jess Hill, See What You Made Me examines the fine lines between love, trust to protect, abuse and power. Through research with riveting storytelling.
COVID-19 and Technology Abuse
With more people at home, working and spending time Online it’s become the weapon of choice of perpetrators. Victims movements can no longer be tracked visually, workplaces are no longer available to be seen-in and public transport is no longer an option to track a victim- Technology abuse is the new norm.
We have seen a triple-digit increase in our Technology Abuse services since the onset of COVID-19 and as each stage of restrictions is applied the demand for our services is increasing. No longer can you drop-in at your workplace and speak to your IT helpdesk team to check the security settings on your phone, no longer can you rely on a friend to pop around to check your social meeting settings, being at home connected to a WIFI network and/or smart home devices is the weapon of choice. Victims every move, every button pushed, every restaurant delivery is potentially being monitored by somebody who wishes harm against you.
Services we offer at Protective Group to disrupt Technology Abuse
We not only eliminate the immediate threat of Technology Abuse, we also through education prevent the future chances of it returning.
Through our group of brands we offer a professional, specialist service for people experiencing Technology Abuse with a particular focus for individuals experiencing Domestic and Family Violence abuse via technology.
Our Technology Abuse services are focused upon disrupting the abuse, reducing further risk and optimising safety. We are able to provide you or your client with enhanced safety and peace of mind through an individualised service to assess technology abuse and the implementation of immediate
interventions tailored to their circumstances.
We bring together years of first-hand experience to stop the abuse then educate the user through first hand experience of how to prevent becoming a victim in the future.
Key principles of our Technology Abuse services:
-Personalised advice and practical demonstrations provided for clients as to how they and their children can use technology safely without fear of further abuse
-An electronic sweep and methodical visual inspection of the client’s car and other possessions for tracking devices that may have been put in place by a perpetrator
-Where possible, immediate interventions to disrupt tracking by perpetrators, their access to the client’s personal information and accounts
-Where forensic IT assistance is required, we can organise this through a third party for an additional fee
-This service may be paired with additional measures to enhance client safety such as our wearable personal duress alarm, the Tek Safe watch*
We also offer Cyber Profiling and Private Investigators for individuals and organizations suffering from Technology Abuse.
Funding may be available through Escaping Violence Payment or support through The Salvation Army Safer in the Home program.
*Additional charges apply.

Technical sweep of home and vehicles
If you feel that you are being stalked or a victim of malicious spyware, hidden cameras and other forms of illegal surveillance we can assist in detecting and removing these threats.

Remote Technology Assessments
We remotely remove any spyware, check social media settings, conduct an electronic sweep for tracking, listening, transmitting and recording devices and reset passwords and security questions.

On-site Technology Assessments
Appointments can be made at our National Support Office located in Melbourne or we can visit a location that suits you or your client. We assess all types of personal devices, major brands and operating platforms.
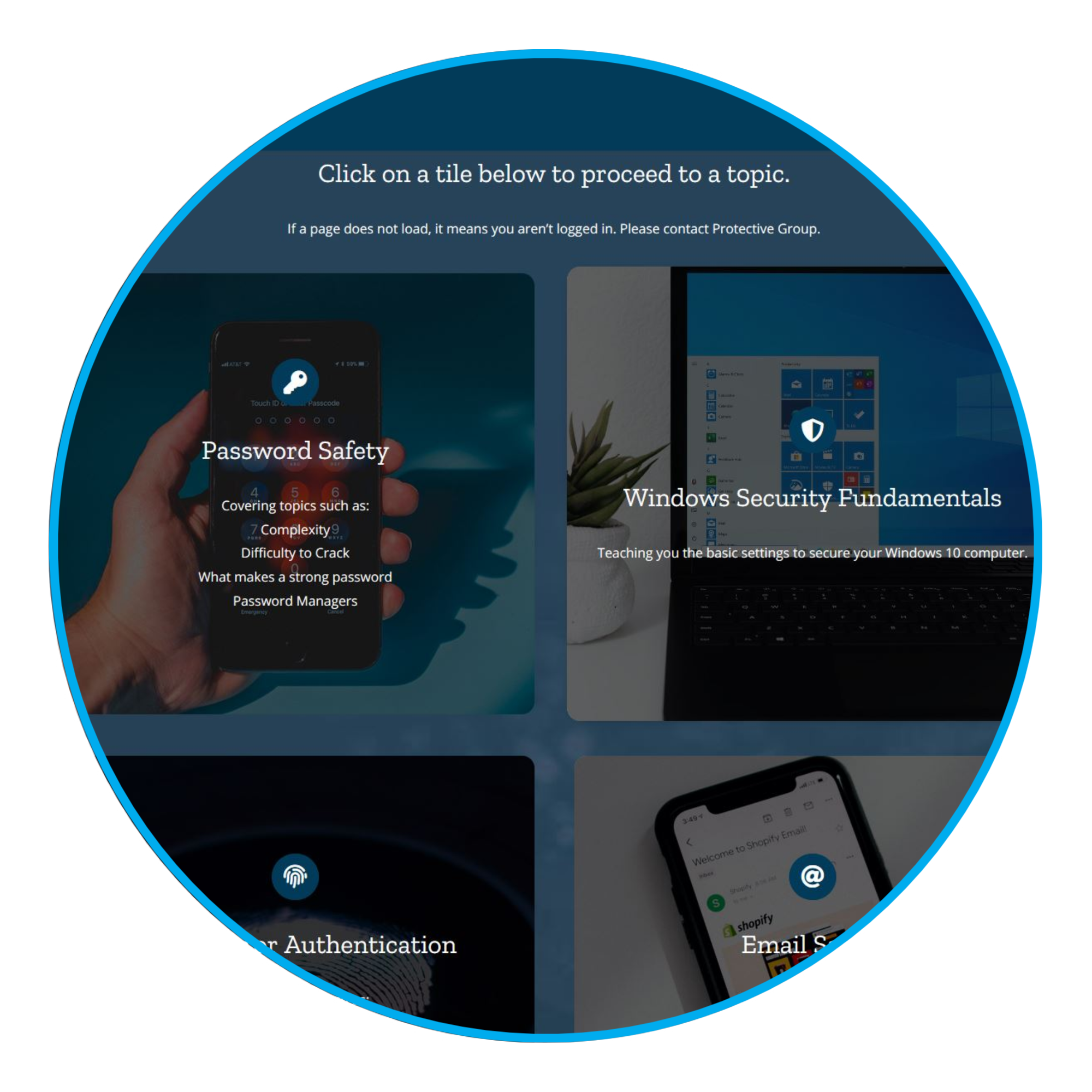
Online Educational Awareness
Our online training covers all aspects of awareness around Technology Abuse, how to secure your networks and devices and reduces risk and exposure to online predators and cyber bullies.